Just over a year ago, ISACA reached out to me asking for my thoughts on digital trust. Of course, I had a few ideas related to the subject, as it had come up in several board meetings I’d been in recently. As it turns out, this short discussion vaulted me into an entire new realm of cybersecurity, privacy, governance, risk and compliance and I can’t turn back now.
Digital trust is the next generation of privacy and cybersecurity, risk and IT governance. If you don’t believe me, read on.
How do I see digital trust?
Let’s take one of my favorite hotel chains, Marriott. I’ll admit it, Marriott has experienced a few issues in the last couple of years. They’ve had a few hacks, been fined for privacy violations under the GDPR, and of course, they’ve overcharged me a few times. You would think that I would have dropped Marriott by now, but I haven’t. I’m still a loyal customer. I’ve talked to other colleagues who removed Marriott from their travel plans due to a few ‘glitches,’ but I’ve chosen to stay with them. This is because I still trust our digital relationship. This got me thinking about digital trust. Why am I still a fan of them when many punted them after the first sign of distress?
This is digital trust.
There are a lot of definitions of digital trust out there. Now that it is becoming a buzzword, everyone seems to have a solution for it. Sure, I’m a huge ISACA fan, but I really like their definition:

To be fully transparent, I was a member of the development team for the Digital Trust Ecosystem Framework (DTEF) with ISACA. It might not be a surprise to you that every word in this definition was evaluated and argued over to make sure we had the most appropriate definition, and I really like how this turned out.
Let’s take this a step beyond just defining digital trust. There are several attributes that build trust. Back to my Marriott loyalty – why did I choose to stay with them when others opted out? For me, there were several factors:
- I’m a longtime member with a lot of loyalty points and a lot of perks when I use Marriott
- I am satisfied with their communications, and approach to negative newsworthy events
- I still trust Marriott’s digital communications and their protection of my privacy
- I prefer to use their app to schedule and manage my stays rather than calling them
- I like their brand
In turbulent times, customer trust is key, and it is easier to lose trust than gain it. Speaking of brand, this is one of several factors that build trust. I was reading an article from a company called Morning Consult, they have done significant research around brand. What I got out of their research wasn’t surprising. They’ve identified the most trusted brands, both internationally and in the United States. Guess what the top trusted brand is? BAND-AID (see the report here). If they get hacked, will you stop using BAND-AIDS? I wouldn’t, for the same reasons I still like Marriott.
Build a Digital Trust Ecosystem
You may be thinking, as I did at first, that this is another consultant buzzword to sell more services and products. Believe me, this is not a passing fad. The proliferation of cybersecurity, privacy, and a myriad of other compliance concerns is vexing companies with overwhelming requirements. So, think of digital trust as 1) an extension of your cybersecurity and privacy programs, 2) a holistic approach to protecting your brand and your consumers, and 3) a means to increasing your reputation while supporting digital transformation and customer loyalty.
What’s more, even the World Economic Forum (WEF) is in this game. Back in November of 2022, the WEF published a report titled “Earning Digital Trust: Decision-Making for Trustworthy Technologies” in collaboration with Accenture, KPMG and PwC. Although the paper was very high level, there is some very important information here that is useful. Take a look for yourself and make your own assessment here.
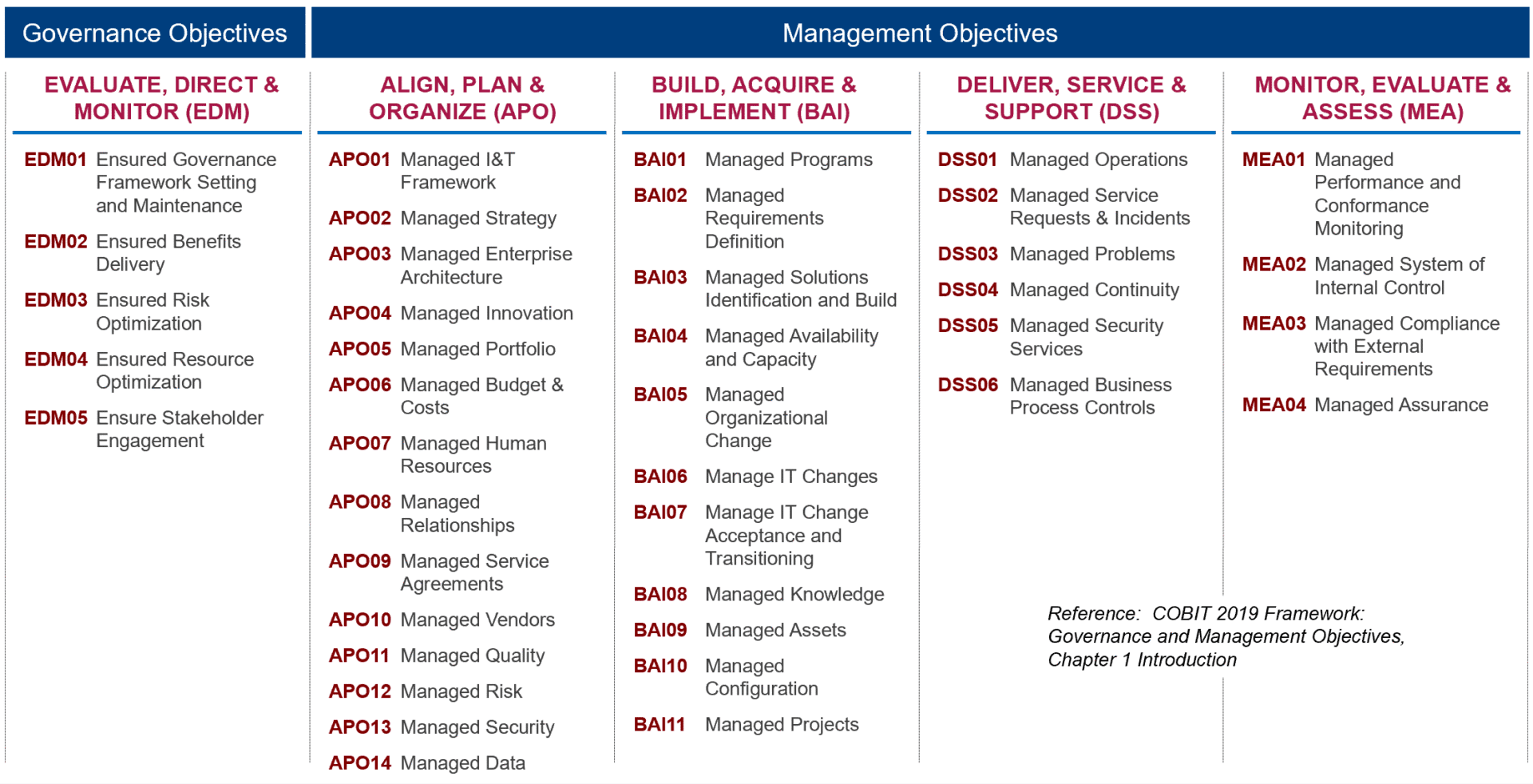
Now, let’s look at the ISACA Digital Trust Ecosystem Framework, or DTEF. I can say without a doubt that this framework really gets into the actionable areas of creating a digitally trusted environment. Think about it, digital trust is more than a bunch of principles. Of course, these are great guideposts, but as a business manager, C-Level executive or board member, I need to know what I should be doing. If you are interested in a really good webinar that explains the framework, and are an ISACA member, check this out.
The DTEF starts at the highest level of the organization, called nodes. Not surprisingly, these include People, Process, Technology and Organization (see the diagram below). Nodes are connected through Domains, which create the dynamic relationships that enable the DTEF to describe the complexities of a system in today’s highly interconnected environment. These interconnections show that the DTEF is not static. They represent the dynamic parts of the framework where actions occur and where changes within the domains influence the nodes.
Thus, an ecosystem.
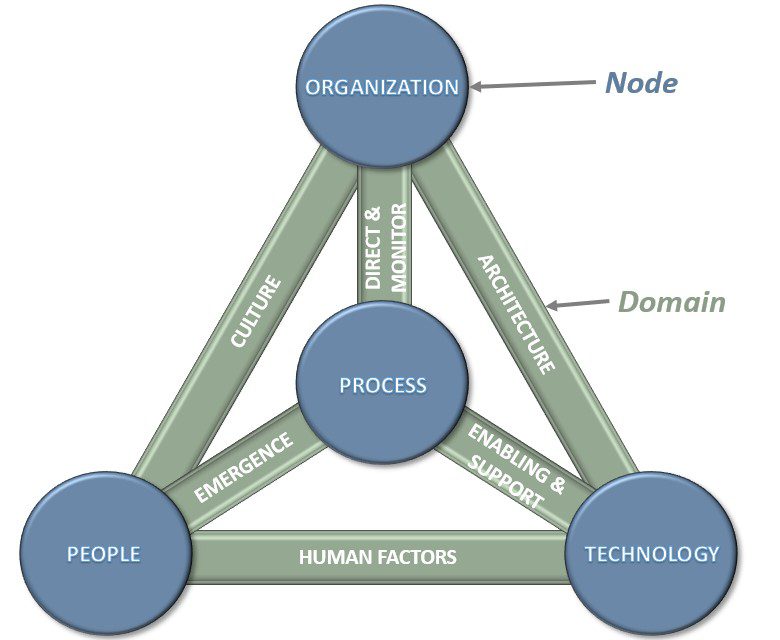
ISACA DTEF Hierarchy (Mark Thomas’ rendition)
Here’s where the DTEF earns the right to be called a framework. The model takes these domains and breaks these down further into trust factors, practices, and activities. All of which are supported with outcomes, and key performance indicators. I have not found another digital trust framework that provides this.
As with any framework, you should NOT expect to copy and paste this into your environment and have digital trust magically appear in your organization. Also, this framework doesn’t replace everything you currently have in production. It is designed to mesh with all your current models used, such as ITIL, COBIT, ISO, NIST, TOGAF and many others.
Top 5 Digital Trust Objectives
I’ve given you a lot of information so far and suggest that you keep an eye out on the ISACA site for more information about the forthcoming DTEF. In the meantime, here’s my top ten five list of things that I’d be looking at if I were a C-Level or board member of any organization that interacts with customers or consumers digitally:
Top tip 1: Know what types of digital interactions you have with your customers and consumers.
Organizations have multiple relationship types. These are determined by understanding the products and services, and stakeholders. The type of digital trust relationship can be a major factor in how digital trust is designed and controlled. There are many types of interactions. These include:
- Business to Business (B2B)
- Business to Consumer (B2C)
- Business to Employee (B2E)
- Business to Government (B2G)
- Government to Consumer (B2C)
- Peer to Peer (P2P)
Top tip 2: Know what products and services are digitally enabled and how you interact with customers and consumers.
Analyze each product and service to determine what digital interactions are required to ensure their proper delivery and support. Look at the entire development and delivery cycle to identify where each product or service might depend on digital solutions, or leverage digital interactions with suppliers, partners, users, customers, consumers, etc. This is important because the product or service lifecycle identifies all the potential digital touchpoints between various stakeholders throughout the deployment process.
Top tip 3: Get digital trust embedded into your governance structure.
No initiative can be successful without proper governance, and the DTEF includes this. Considering digital transformation usually occurs in a high-velocity and fast-paced environment, it is important to ensure that risks are addressed, authorities are defined, and governance components are considered.
Consider creating a governing body to oversee digital trust efforts. Governing bodies typically start at the highest level of the organization: a board of directors, board of regents, or an equivalent of these. Each board receives and disseminates information using committees. Examples of these committees include the strategy, finance, governance, compensation, and audit committees. However, throughout the organization there are several governing bodies who are chartered to prioritize efforts, allocate funding, and address escalations. These bodies are often not considered governing bodies of organizations – but in reality, they are. A digital-related committee could provide the governance over enterprise digital trust. If this is not a viable option for your organization, you should at least have digital trust embedded as a topic for the board and each committee.
Don’t forget about risk. The risk register is a list of risk areas that have been identified, analyzed, prioritized and either accepted, transferred, avoided, or mitigated. It is not just a list of control deficiencies or missing software patches from a server, rather, it is an inventory of events that could affect or prevent the organization from meeting its goals and objectives.
Top tip 4: Create use-cases for all digital interactions with your customers and consumers and use these to help you select the appropriate trust factors.
A use-case describes how an actor interacts with an organization through a digital solution to accomplish one or more of that actor’s goals. It is a full description of the attributes and steps that are required to accomplish a specific goal. The creation of use-cases is a critical step in digital trust. Knowing these can help identify the appropriate domains and trust factors that are key to a trusted digital ecosystem. Use cases could include the following:
- Product or Service
- Relationship Type
- Relationship Medium
- Inputs or Preconditions
- Interaction Description
- Outcomes or Post Conditions
- Related Use Cases
- Stakeholders
- DTEF Relationships
Top tip 5: Use the ISACA DTEF to guide you in adopting the appropriate trust factors to support your digital trust efforts.
Keep an eye out for the DTEF and any supporting publications from ISACA regarding digital trust. No single body of knowledge thoroughly addresses the scenarios, risk and controls required to operate in a digitally trusted environment. The references I’ve found so far focus on a single industry, organizational goal, or type of transaction/interaction. To provide a holistic view of the complete digital trust ecosystem, go to the DTEF.
ISACA’s DTEF supports the establishment and maintenance of digital trust from multiple perspectives. Digital trust is broader than just technology; it applies to the entire organization and to all its external stakeholders as well. You may have heard of this as the digital supply chain. Selecting, establishing and maintaining digital relationships requires confidence and transparency from all parties involved. However, the needs, principles, values and objectives of providers and consumers influence the levels of trust.
Bonus tip: Adopt digital trust iteratively over time.
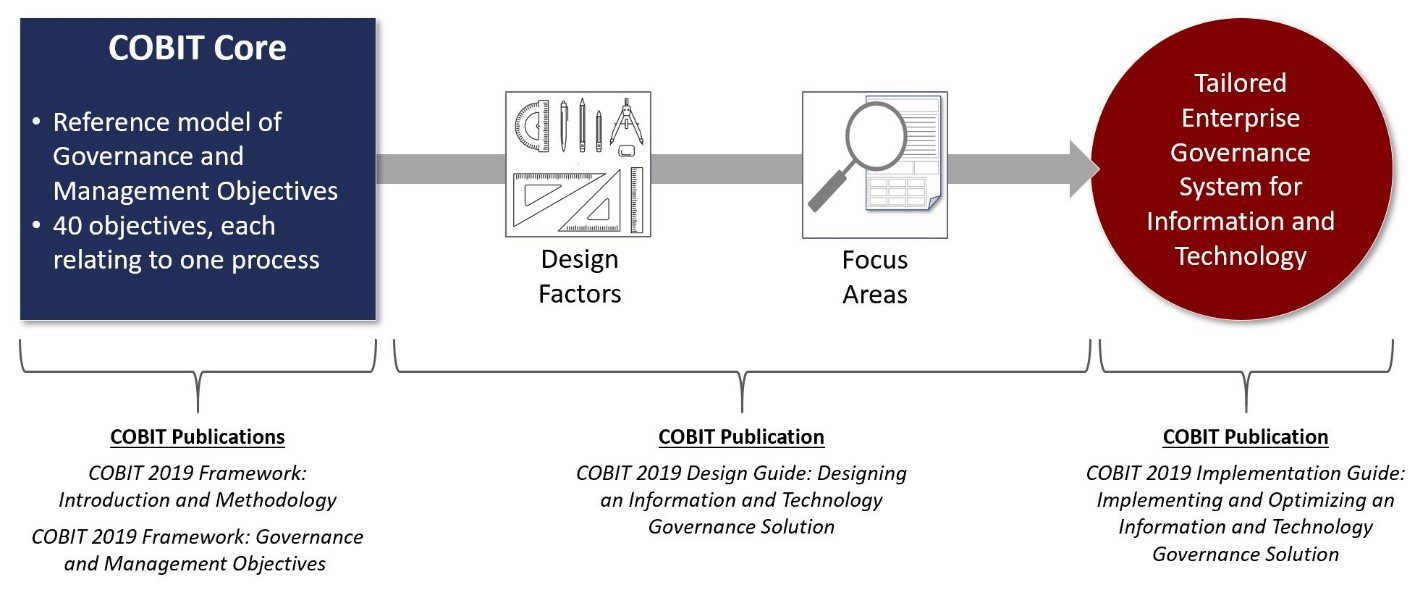
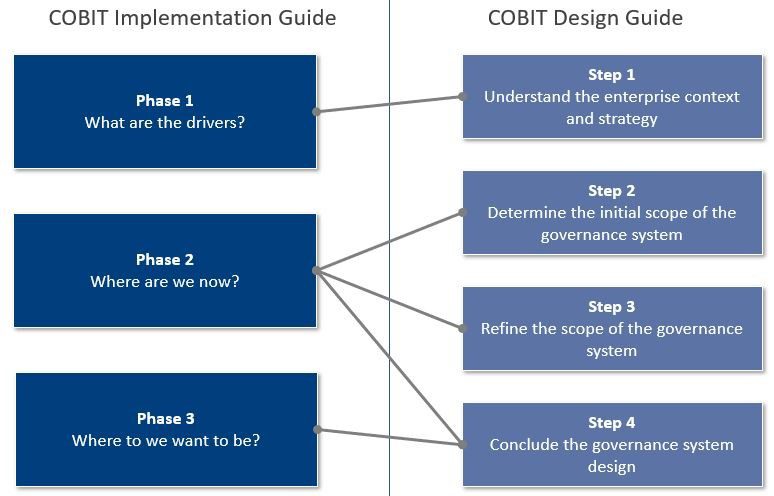
It may seem a little biased for me to add COBIT to the mix here since I’m a huge COBIT fan, but I believe the COBIT Implementation model is one of the most comprehensive and complete guides to implementing almost ANYTHING. The COBIT 2019 Implementation Guide emphasizes an enterprise-wide view of governance of I&T and can also be used for digital trust initiatives.
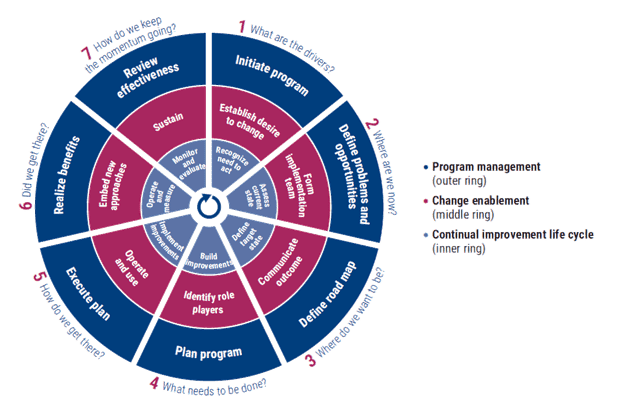
COBIT Implementation Model (ISACA)
The continual improvement life cycle approach allows enterprises to address the complexity and challenges typically encountered during an enterprise governance of information and technology (EGIT) implementation, and by extension, a digital trust initiative. If you haven’t given it a look, maybe now is the time.
A quick summary
You can be secure, you can protect customer privacy, and you can be compliant, but if your customers or consumers don’t trust you, you’re out of business. No organization is immune to a negative newsworthy event, and if that happens, it’s most likely too late to think about creating digital trust because your customers and consumers have already calculated their losses. As with my Marriott experience, they had more than one event, but I’m still a loyal customer because they recognized how to build trust in their digital interactions with me. Don’t treat cybersecurity, privacy, information technology, risk, and digital transformation as separate functions in your organization. Think of these as integrated components to digital trust. To do this, I’d keep an eye on the ISACA DTEF for guidance. Today, it is the most comprehensive tool to consider all aspects of digital trust in the people, process, technology and organization areas.
As always, I hope you’ve learned from this post. Please let me know what you think. Email me at mark@escoute.com with your support, questions or challenges to this post – my SLA is a 48 hour response 😊